Improve your data collection and analysis!
Rezenent will enable you to define, collect, analyze, and make informed decisions that Resonate.
How can Rezenent help you with Cyber Security?

CMMC Preparation and Certification
The Cybersecurity Maturity Model Certification (CMMC) is a unified standard for implementing cybersecurity across the defense industrial base (DIB), which includes over 300,000 companies in the supply chain. The CMMC is the DoD's response to significant compromises of sensitive defense information located on contractors' information systems. There are three levels to the CMMC:
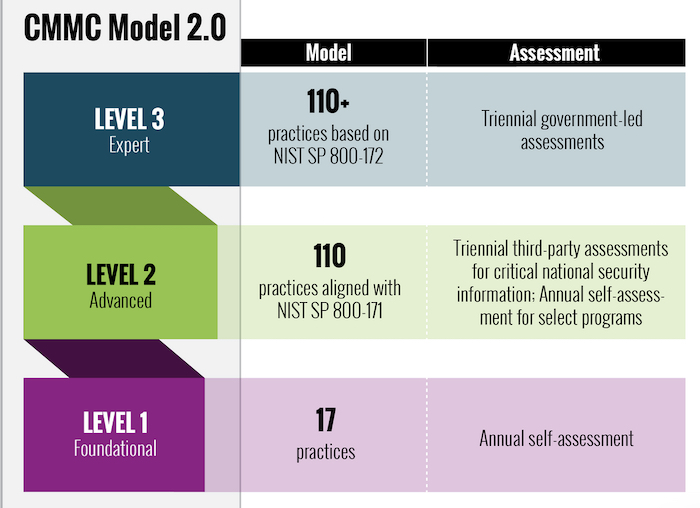
Rezenent can aid an Organization Seeking Certification by:
- performing a self-assessment for Organizations seeking Level 1 certification
- participating on an Assessment Team as a Certified CMMC Professional (CCP) (PENDING) for Organizations seeking Level 2 certification from a Certified Third-Party Assessment Organization (C3PAO)
- preparing an Organization seeking any level of certification by collecting and cataloging evidence, performing mock interviews, and testing procedures

DFARS Self-Assessment
The Defense Federal Acquisition Regulation Supplement (DFARS) to the Federal Acquisition Regulation (FAR) is administered by the Department of Defense (DoD). DFARS implements and supplements the FAR. DoD government acquisition officials and contractors and subcontractors doing business with the DoD must adhere to the regulations in the DFARS.
Contractors and subcontractors must undergo a DFARS self-assessment and submit their score to the Supplier Performance Risk System (SPRS) by November 30, 2020 in order to be awarded new federal contracts or options on current contracts.
Rezenent can help prepare documentation for the self-assessment, execute the self-assessment, and aid in submitting scores to SPRS.

ITAR Registration
The International Traffic in Arms Regulations (ITAR) is the United States regulation that controls the manufacture, sale, and distribution of defense and space-related articles and services as defined in the United States Munitions List (USML).
Besides rocket launchers, torpedoes, and other military hardware, the list also restricts the plans, diagrams, photos, and other documentation used to build ITAR-controlled military gear. This is referred to by ITAR as "technical data".
Rezenent can help develop policies and procedures, register on the Department of State's Directorate of Trade Control (DDTC) website, and submit your application for ITAR registration.
Other Services
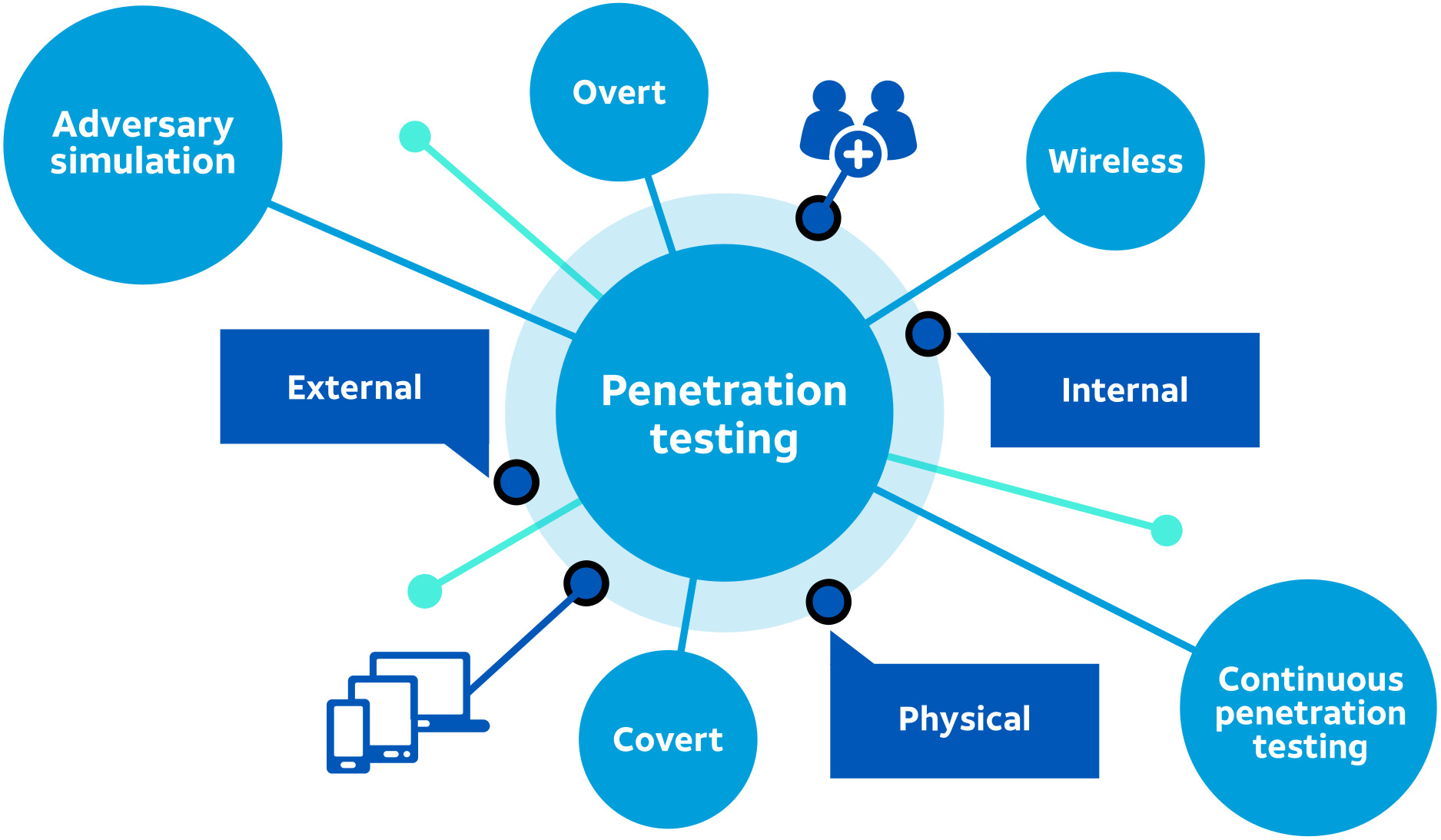
Penetration Testing
A penetration test, or pentest, is an attempt to evaluate the security of an IT infrastructure by safely trying to exploit vulnerabilities. These vulnerabilities may exist in operating systems, services and application flaws, improper configurations or risky end-user behavior. Such assessments are also useful in validating the efficacy of defensive mechanisms, as well as end-user adherence to security policies.
Rezenent has taken the Offensive Security Certified Professional (OSCP) course (Certification Pending) and can safely conduct pentests externally with little to know information via Open source intelligence (OSINT) or internally with the aid of a trusted insider.
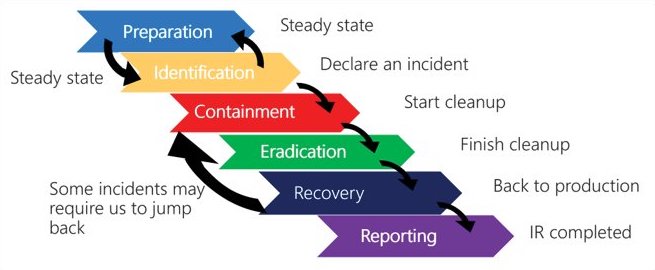
Security Incident Management
Incident response is an organized approach to addressing and managing the aftermath of a security breach or cyberattack, also known as an IT incident, computer incident or security incident. The goal is to handle the situation in a way that limits damage and reduces recovery time and costs.
Rezenent can act as the Project Manager directing, tracking, and documenting activities of principals, attorneys, in-house and outsourced IT providers and staff, insurance carriers, and law enforcement. Rezenent can also act as Data Analyst with the volumes of collected data identifying the Bad Actor's path if ingress into the network, a timeline of activities and assets possibly compromised, and verify the threat has been contained and eradicated so that recovery may begin.